🌉 The Unsung Hero: Understanding Trezor Bridge
🌉 The Unsung Hero: Understanding Trezor Bridge
In the world of cryptocurrency, where security is paramount, the Trezor hardware wallet stands as a trusted fortress for digital assets. It embodies the concept of "cold storage," keeping your precious private keys offline and out of reach from online threats. But how does this offline device communicate with the online world of your web browser or desktop application to actually let you manage your crypto? The answer lies in a clever, quiet piece of software called the Trezor Bridge.
Often overlooked, the Trezor Bridge is the unsung hero that allows for a seamless, secure, and reliable connection between your physical Trezor device and your computer's software interface, such as the Trezor Suite Web or supported third-party wallets.
What Exactly is Trezor Bridge?
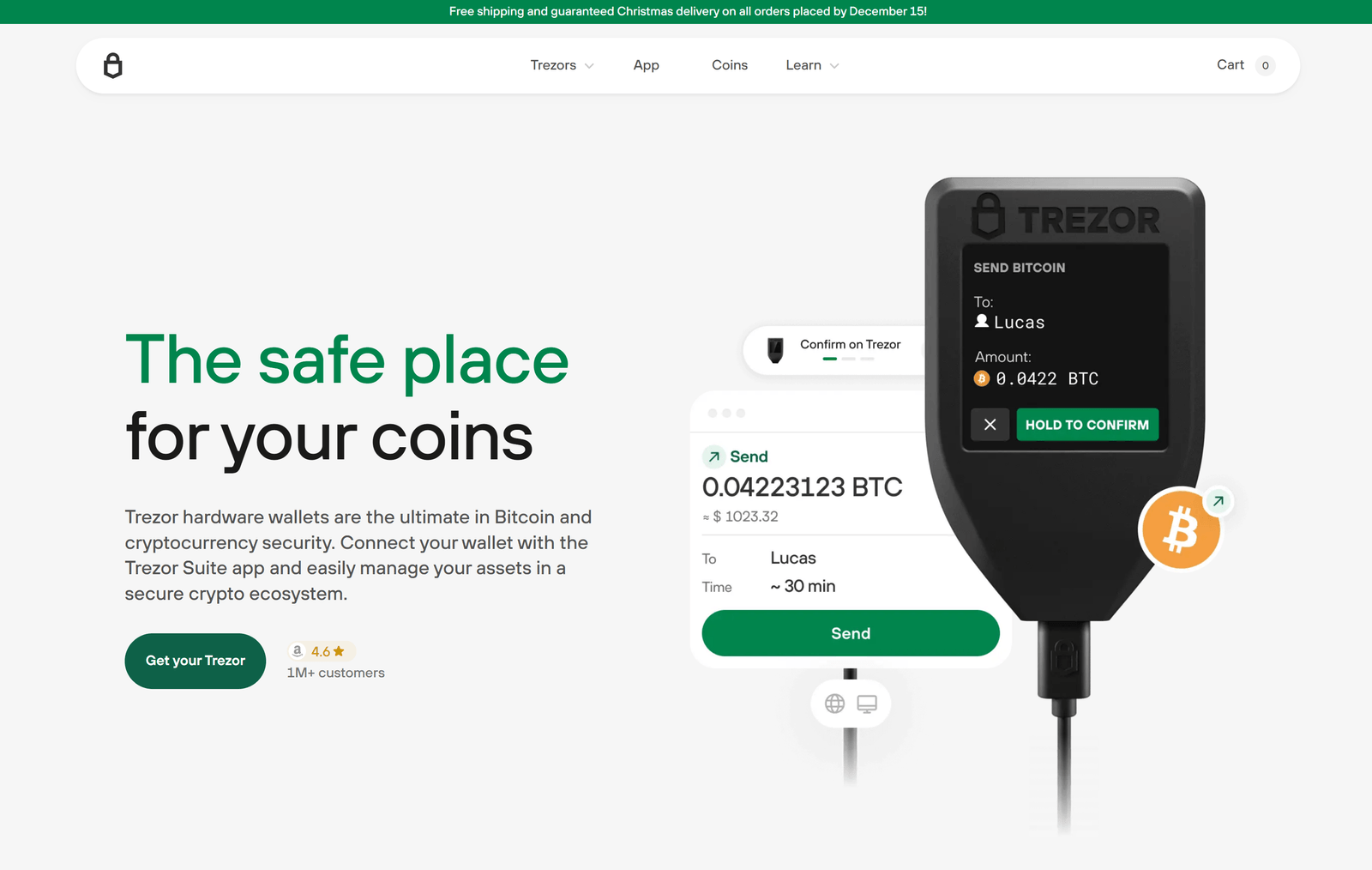
Trezor Bridge is a lightweight, dedicated application that runs silently in the background of your computer (Windows, macOS, or Linux). Its sole and vital purpose is to act as a secure intermediary—a 'bridge'—between the USB-connected Trezor hardware wallet and the browser-based applications that need to talk to it.
When you connect your Trezor, your web browser often cannot communicate directly with the device's USB port for security and technical reasons. Trezor Bridge bypasses these limitations. It essentially creates a local, secure communication channel on your computer, listening on a specific port. Any command a web application needs to send to the Trezor (like a request to sign a transaction) is securely routed through the Bridge.
How the Bridge Ensures Security and Functionality
The design of the Trezor Bridge is a masterclass in combining usability with uncompromising security. Its role is central to the Trezor experience:
1. Facilitating Secure Communication
The most critical function of the Bridge is to establish an encrypted link between the software interface and your Trezor. This is vital because the Bridge ensures that transaction requests, balance checks, and authentication prompts are transmitted securely.
It is crucial to understand what the Bridge does not do: it never has access to your private keys. The core principle of a hardware wallet remains intact. When you initiate a transaction:
- The application (e.g., Trezor Suite Web) sends the unsigned transaction request to the Bridge.
- The Bridge securely relays this request to your physical Trezor device.
- Your Trezor internally signs the transaction using the private key, which never leaves the device.
- The signed (but keyless) transaction is sent back through the Bridge to the application.
- The application then broadcasts the signed transaction to the blockchain.
2. Overcoming Browser Limitations
Many web browsers restrict direct access to USB devices to prevent potential security exploits. Trezor Bridge cleverly works around this. By running locally on your operating system, it provides a stable, standardized way for any supported browser (Chrome, Firefox, etc.) to reliably interact with the hardware, guaranteeing high compatibility without relying on potentially vulnerable browser extensions or plugins.
3. Enhancing User Experience
Once installed, the Bridge operates automatically. It instantly detects your connected Trezor device, enabling quick, seamless interactions. This background automation removes technical barriers and potential connection errors, simplifying the entire process of managing your cryptocurrency for both advanced and beginner users.
Installation and Integration with Trezor Suite
For many users today, the Trezor Bridge is no longer a separate, standalone installation. Trezor, the device's creator, has bundled the functionality of the Bridge directly within its official desktop application, Trezor Suite.
The Trezor Suite is a modern, comprehensive application that combines portfolio tracking, exchange features, and device management. When you install Trezor Suite, the Bridge components are automatically installed with it. This integration ensures that whether you prefer using the desktop Suite application or the web-based version, the secure communication layer is ready to go without any extra manual steps. If you are using an older, browser-only interface, you might still need the standalone Bridge, but the Trezor Suite is now the recommended solution for the best experience.
Security: Is Trezor Bridge Safe?
Given its vital position as a communication link, users often ask about the security of the Bridge itself.
- Open Source: Trezor Bridge, like all Trezor software, is open-source. This means its code is publicly available for peer review and security auditing by the crypto community, ensuring transparency and reducing the risk of hidden backdoors.
- Private Key Isolation: As mentioned, the Bridge never touches your private keys. Even if the Bridge software or your computer were somehow compromised, your private key—the actual key to your funds—is protected by the physical hardware barrier of the Trezor device.
- Physical Confirmation: All critical actions, such as signing a transaction, still require your physical confirmation on the Trezor device itself. You must verify the recipient address and amount on the device's screen. If a hacker somehow managed to alter the transaction details being sent to your computer screen, the correct, uncompromised details will still appear on the Trezor, allowing you to reject the malicious attempt.
A Necessary Component
The Trezor Bridge may be a background utility, but it is indispensable. It is the critical technological component that allows the unparalleled security of an offline hardware wallet to coexist with the convenience of an online cryptocurrency application. By creating a secure, invisible communication channel, the Trezor Bridge ensures your crypto management is reliable, user-friendly, and, most importantly, keeps your private keys exactly where they should be: safe inside your hardware fortress.